Stay Informed: The Latest Insights in OSINT, Threat Intelligence, and Security
At Liferaft, we dive deep into the ever-evolving world of open-source intelligence (OSINT) and security. Our blog is your gateway to insightful analysis, expert commentary, and the latest trends shaping the landscape of threat intelligence, social media monitoring, and executive protection. Whether you’re managing a GSOC, navigating the complexities of SOCMINT, or exploring the nuances of alternative social platforms, our posts offer the knowledge and tools you need to stay ahead in a rapidly changing environment.

Supply Chain Security: 3 Ways Threat Intelligence Can Be Your Predictor
Subscribe to get our latest posts straight to your inbox once a month.
More Posts
Geospatial Intelligence: Enhancing Threat Detection & Response
Corporate security professionals are utilizing the power of geospatial intelligence to transform their risk management and decision-making processes more today than ever, as..
Understanding and Mitigating Insider Threats: Guide for Organizations
Insider threats pose a significant risk to organizations of all sizes across industries. To protect your company's sensitive data and assets, it's crucial to understand what..
2025 Predictions for the Threat and Cyber Industries
As we move deeper into the digital age, the landscape of intelligence is evolving rapidly. In this recent discussion among industry experts Neil Spencer, Mike Evans, and Jordan..
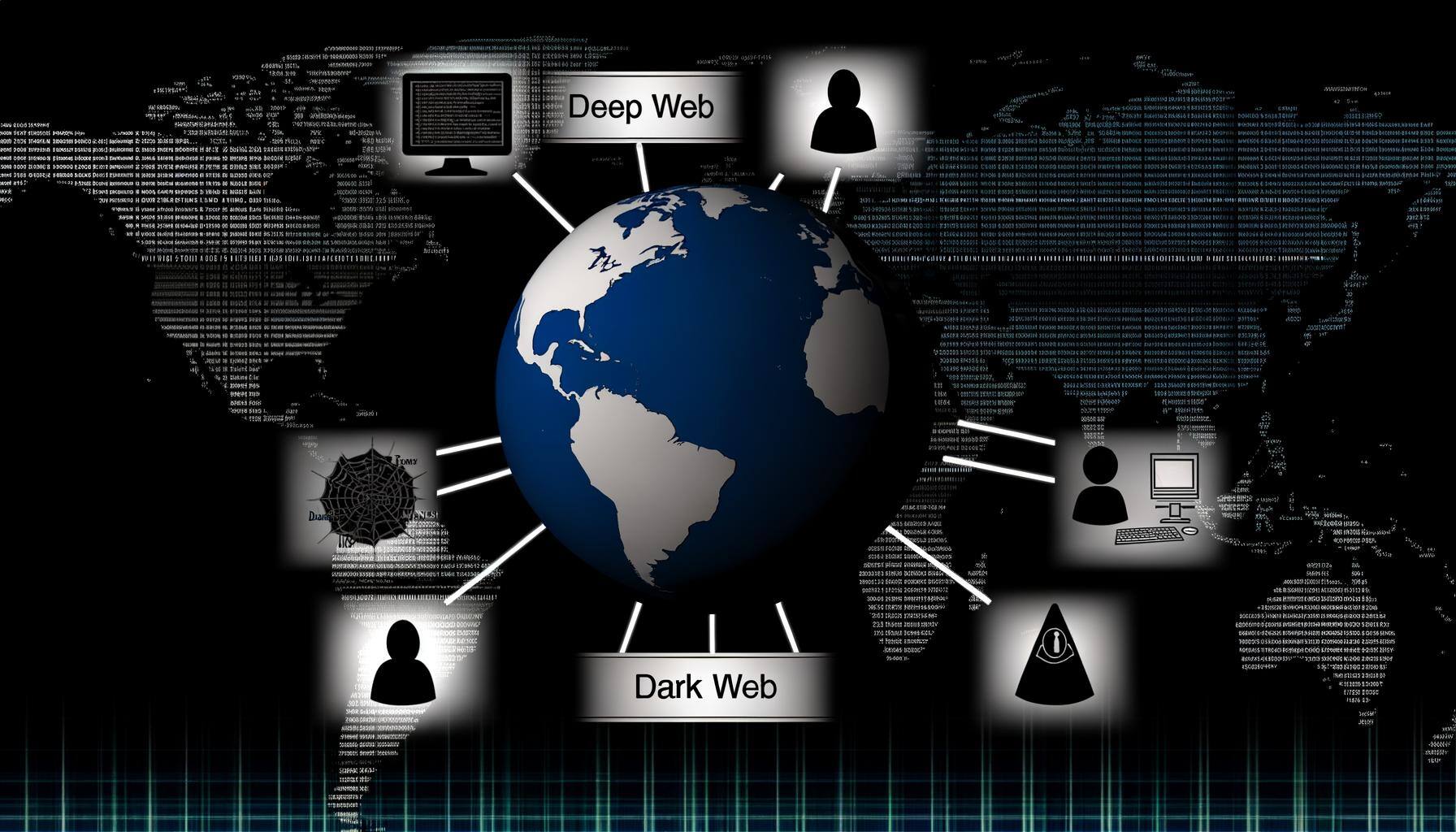
Understanding the Deep Web vs. the Dark Web
The Deep Web and Dark Web have murky origins that trace back to the early days of the Internet. These hidden realms were created for various reasons (some purposeful), leading to..
The 10 Ultimate Threat Intel Strategies You Need to Know
In today's rapidly evolving digital landscape, the importance of threat intelligence cannot be overstated. By proactively identifying and mitigating potential threats,..
The World of IoT (Internet of Things)
Connected by digital systems and devices, we live in the Internet of Things (IoT). IoT is a network of physical things that exchange data. Whether it’s an iPhone, Tablet, Alexa,..
What is a Protective Intelligence Program and How is It Used?
It's no secret that too many bodyguards take a ‘guard at the gate’ approach to keeping their principal safe. In other words, they wait for something to go wrong and then respond..
What is the Deep Web? A Quick Guide for Beginners
Want to know a secret? There’s a huge portion of the web that you can’t access through a traditional search engine.
Our Top 9 Blog Posts and Podcasts of 2023
As we reflect on the past year, LifeRaft is proud to have been at the forefront of delivering cutting-edge insights and knowledge to corporate security professionals. Staying..
Popular Post

Beyond the Front Door: Why Threat Monitoring & Physical Security Must Work Together
Threat Intelligence, Workplace Violence
Learn why physical security alone isn’t enough. Discover how threat monitoring provides early warning to prevent workplace violence before it starts.