
Contents
At Liferaft, we know from talking to security professionals that many teams struggle with social media threat monitoring.
Each day, users post billions of messages. Even a well-staffed detail can’t shift through that much content to uncover bad actors or spot security risks.
Some people describe the situation like a game of ‘Where’s Waldo?’. But that metaphor seems somewhat overused and falls short of the real experience.
It seems more apt to describe the problem like a ‘BOLO alert for lanky backpacker somewhere in Europe.’
Feels hopeless, doesn’t it?
What’s worse? Nowadays, gathering intel online requires more and more technical expertise. But for those without formal OSINT training, the learning curve feels intimidating.
Fortunately — a small silver lining — you have a number of ways to tackle these issues.
Teams can dramatically improve the effectiveness of their social media threat monitoring programs by addressing a handful of common mistakes.
Let’s go through the top seven, one by one, and figure out how to fix them.
1. Casting a Small Net for Data Collection
Most security teams that conduct social media surveillance watch the big platforms: Facebook, Instagram, Twitter, TikTok.
But over the past few years, millions of people have migrated to a growing collection of ‘alt-tech’ social networks.
This presents a challenge for analysts.
If a threat actor posts something on one of these new sites, it could slip past your team undetected.
You might get caught off guard by a threat that you later discover was published right in plain sight.
Alternatively, investigations are rarely confined to one platform.
An analyst may discover a bad actor on one site. Then they might follow a trail of breadcrumbs across multiple networks to evaluate the severity of the threat.
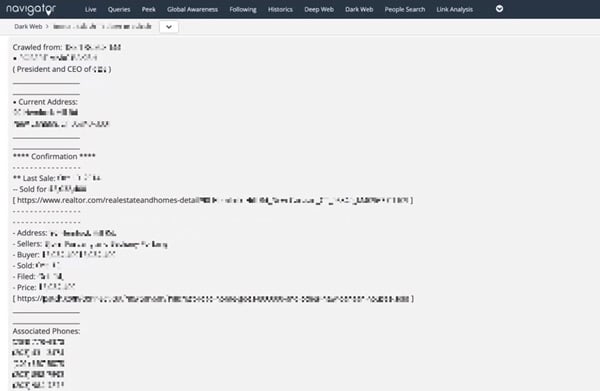
Doxxed personal information of a corporate executive on the darknet, including wi-fi passwords, home address, and family member details, discovered by Navigator.
How to Fix This: Go beyond the standard list of social media platforms. Analysts need to keep an eye on the lesser-known corners of the web — paste sites, darkweb forums, alt-tech social networks, etc. The wider your coverage, the less likely you are to overlook a critical threat.
2. Failing to Cover Your Digital Tracks Online
Each time you go online, you leave a trail of digital breadcrumbs to onlookers: IP addresses, keyboard configurations, device operating systems, etc.
Many people might use the same settings and hardware. But your unique patterns online can serve as a type of cyber fingerprint.
And those patterns can tell a lot to others about your identity and activities.
What does that mean for the open source investigator?
In the worst-case scenario, these cyber fingerprints can reveal to a person of interest that they’re the target of an investigation.
Once alerted, they might start to delete evidence, conceal their activities, or retaliate against your organization. All of which can create headaches for you and your team.
For instance, say hypnotically you begin investigating a POI on Facebook.
Let’s imagine further you’ve taken no efforts to cover your digital tracks. Maybe you even log onto the site using your personal account on a corporate network. (Not good!)
Without any attempt to conceal your activities, Facebook deduces you and your target have some sort of relationship.
And all too often, the algorithm may then suggest your profile in their feed as a ‘Friend Suggestion.’
That’s the OSINT equivalent to showing your hand at the poker table.
Social media serves as your window to look at the world. But don’t forget that the world can also look back at you.
How to Fix This: At LifeRaft we highly recommend using a managed attribution service — such as our partner Authentic8. These technologies disguise how your online activities appear to third parties. This allows you to conduct investigations with more anonymity. And by extension, that reduces the chances of tipping off adversaries.
3. Overlooking Accidental Insider Threats
Most security awareness programs tend to focus on nefarious actors; organized crime, violent customers, malicious employees.
But increasingly, leaders have learned it’s the ‘accidental insider threats’ that often present the biggest risk to organizations.
Accidental insider threats represent ordinary, well-intentioned employees.
Oftentimes, their actions are the result of a general ignorance of safety protocols. Or perhaps they’re looking to work around security procedures to finish an assignment.
Regardless, their activities online can compromise safety. And it’s a type of risk few businesses actively look out for.
A common incident, for instance, occurs when an excited employee starts their first day at work.
They may post a message on social media about arriving at their new office alongside a picture of their entry ID.
Nefarious outsiders, however, can use this image to print their own fake ID cards.
That would make it easy to trespass on company property or access secured facilities.
How to Fix This: Monitor for mentions of your organization’s name alongside keywords like ‘first day at work,’ ‘got my ID card,’ or ‘office photo.’ If you’re responsible for VIP protection, be sure to survey the social media activities of a principal’s close contacts. All too often, these scans reveal accidental leaks of confidential information.
4. Forgetting to Document Findings
New investigators often dive right into their assessment.
But when it comes time to summarize the results of this investigation, their notes are missing dates, URLs, timestamps, and other references.
Backtracking to uncover these details creates a lot of extra work. And it represents the quickest way to annoy managers or colleagues.
To make matters worse, the internet is a volatile place.
Users delete posts. Social networks suspend accounts.
In other words, content you see online today may vanish at any moment. If you fail to record a post or article, it can compromise your investigation down the road.
How to Fix This: Record all of your findings during the course of an investigation, along with dates and timestamps. To accomplish this, analysts can use a growing number of free and paid tools. Or documentation can be done manually. Regardless of which method is chosen, your future self will thank you.
5. Ignoring the Wider Social Media Landscape
Over time, users migrate from one social platform to another. If you miss these trends, it’s easy to overlook new threats.
Imagine yourself as an intelligence agent eavesdropping on conversations at the local Starbucks. But if the enemy spies meet at Dunkin’, you won’t pick up any useful information.
You need to hang out where threat actors conjugate.
A few years ago, for instance, organized criminal groups once shared tips over the big social networks. But moderators soon started to crack down on their activities.
In response, thieves moved to new online spaces. Some of the most popular include alt-tech platforms like Raddle.me and Telegram.
Thing is, many security pros have never heard of these sites. And even fewer actively monitor them.
 A shoplifting how-to guide for a large retail brand on Raddle.me, discovered by Navigator.
A shoplifting how-to guide for a large retail brand on Raddle.me, discovered by Navigator.
How to Fix This: Stay up to date on new and emerging social networks. Small, little-known sites often represent hotbeds for criminal activity or violent extremists. In our Social Media Threat Monitoring Crash Course, you can find a handy list of sites we recommend teams watch when conducting surveillance.
6) Piggybacking Off of the Marketing Department
Some security teams piggyback off of the social media listening tools used by their marketing department.
In theory, this allows you to quickly automate a threat monitoring program. And you can pull this off without investing in new software.
But this approach has two problems.
First, these software tools often have slow crawl times. In other words, they only pull in data from platforms every few hours.
That doesn’t present an issue for marketing teams. Advertisers rarely need real-time data.
But in the event of a crisis, slow crawl times can cost responders precious minutes or even hours.
Second, marketing tools focus almost exclusively on the biggest social networks. Few cover alt-tech platforms, obscure forums, or darkweb content.
As mentioned above, that can represent a major oversight as more and more users migrate to these communities.
How to Fix This: Managers should consider tools that cater specifically to security teams. Before selecting a vendor, be sure to ask about crawl times and breadth of coverage.
7) Conducting Manual Surveillance
Many security teams attempt to conduct social media surveillance manually.
But the internet is a big place. Even a well-staffed team can’t watch every nook and cranny of the web.
Worse, manual surveillance represents a time-intensive endeavor.
That usually means analysts have to limit the scope of threats they’re on the lookout for. Or perhaps they only have time to watch a few big platforms.
All of which make it more likely you’ll miss something important.

A screenshot of Navigator’s Sentiment Analysis and Data Insights Dashboard
How to Fix This: The more your team can automate routine tasks, the more data you can collect and analyze. For leaders, this allows them to stretch limited budgets. For analysts, it reduces the chance of missing relevant intel. It also allows team members to spend more time analyzing and responding to threats rather than gathering data.
Wrapping it up…
Don’t beat yourself up too much if you discover you’re breaking a few of the points listed here.
Many experienced analysts made these mistakes while developing their skill set. And even the best slip up from time to time.
But use this list as insight to step up your surveillance program. After all, effective social media threat monitoring can go a long way towards keeping your people, customers, and property safe.