Social media platforms have emerged as crucial tools for identifying early warning signs of potential security threats. By diligently monitoring these channels, security professionals can anticipate emerging risks and implement proactive measures to address them effectively.
Setting Up Effective Social Media Monitoring
To establish a robust social media monitoring system for threat intelligence, consider the following steps:
Utilize OSINT Tools Made for Threat Intelligence Teams: Select social media monitoring tools that suit your organization's needs. For effective threat detection on social media, you have to go beyond mainstream monitoring tools like Hootsuite. The best tools for threat intelligence teams are those that can layer in mainstream social posts correlated with posts found on alternative platforms like Gab and Telegram.
Establish 'Include' and 'Exclude' Keywords and Parameters: Determine pertinent keywords, hashtags, and geotags that relate to your security issues. This should encompass your organization's name, industry-specific terminology, phrases associated with events, and the names of key employees with high visibility.
Configure Real-Time Alerts: Set up your chosen tools to send immediate notifications for relevant mentions, ensuring prompt responses to potential threats. Ensure the tool you select supports both mobile and desktop alerting effectively.

Key Indicators and Red Flags
Monitoring social media for key indicators and red flags is crucial for effective threat detection and risk mitigation.
Key indicators and red flags serve as an early warning system for potential threats. By identifying these signals early, organizations can take proactive measures to prevent or mitigate risks before they escalate into more serious problems.
When monitoring social media platforms, watch for these potential threat indicators:
Unusual Activity Spikes: Sudden increases in mentions of your organization or related keywords
Negative Sentiment: A shift in tone towards your brand or industry
Coordinated Campaigns: Multiple accounts sharing similar messages or using identical hashtags
Geolocation Patterns: Clusters of posts from specific locations that may indicate physical threats
Lastly, being mindful of key indicators and red flags can expeditiously help spot cases of insider threats.
Monitoring employee social media activity, while maintaining respect for privacy boundaries, can be an effective strategy for detecting potential insider threats. Certain red flags may indicate a risk, such as expressions of job dissatisfaction, the sharing of sensitive company information, or an unusual interest in restricted areas or data.
Case Studies of Social Media-Detected Threats
Executive Protection
Imagine receiving alerts that top executives at your company have been threatened with violence. As an intelligence analyst, you must quickly identify the threat and act before it’s too late. That’s precisely what happened to a global oil & gas company in 2023, whose intelligence team received alerts of online posts threatening to kill their CEO and another top executive.
By automating the collection of these posts, the team saved hours of investigative time and was able to conduct identity resolution with the click of a button. This critical time saved allowed the team to implement a protection plan and avoid a violent outcome.
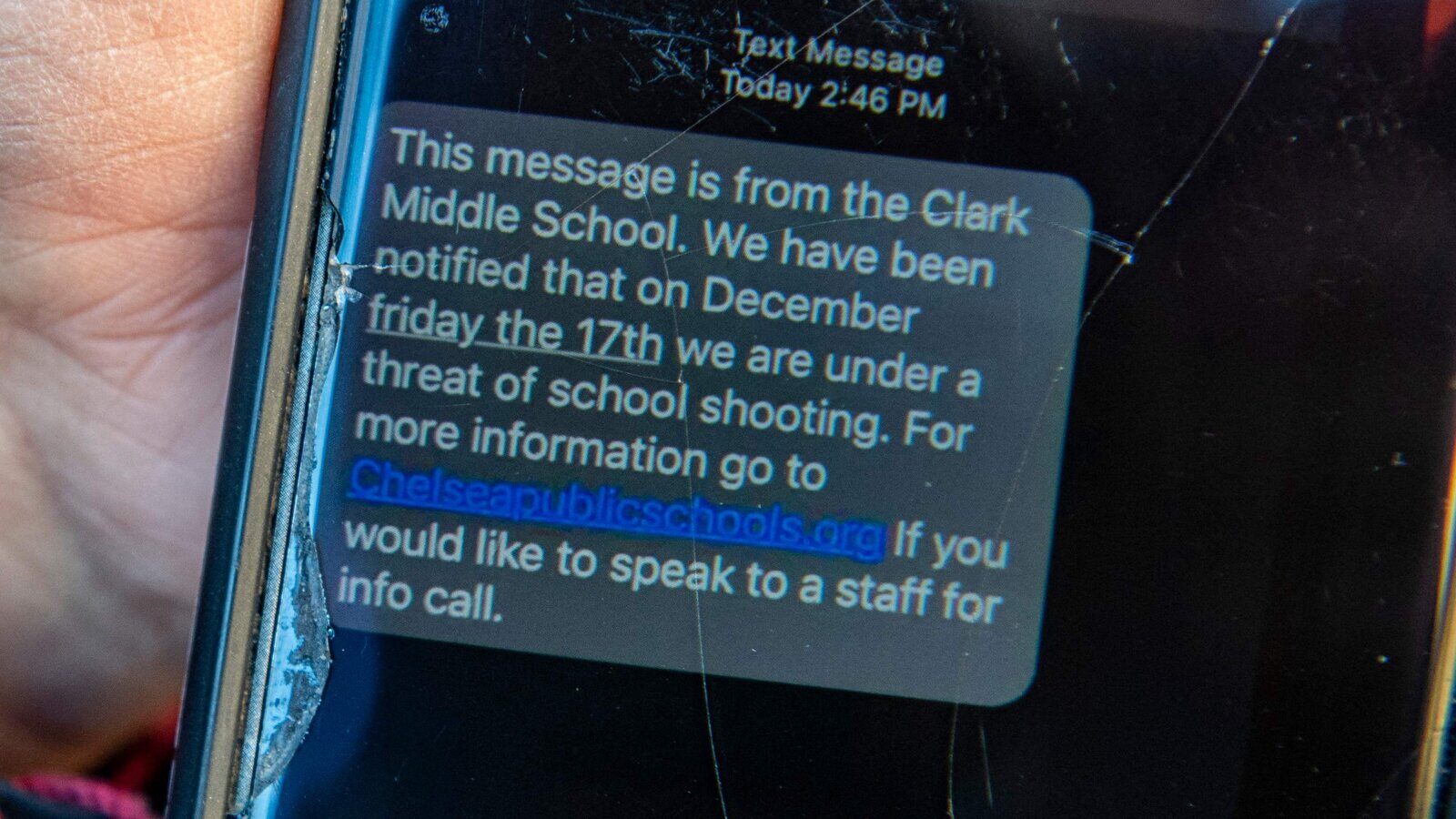
image courtesy of the New York Times
School Shootings - Duty of Care
In December 2021, a surge of threats related to school shootings spread across TikTok and various social media platforms, featuring numerous videos that included warnings about a potential bombing or shooting scheduled for December 17, 2021. While these threats were ultimately deemed not credible, many school districts and law enforcement agencies responded seriously by canceling classes and enhancing security measures. Their actions ensure that should events like this occur again and effective monitoring in place, the lives of thousands of children would be saved.
Conclusion
As seen in the case studies above, social media monitoring for early threat detection not only saves lives, but is a must in many industries for compliance reasons.
Additionally, awareness of potential legal issues discussed on social media (e.g., copyright infringement, defamation) can also help organizations avoid legal complications.
Organizations can transform the vast amount of social media data into actionable intelligence by focusing on key indicators and red flags. This targeted approach improves threat detection capabilities and enhances the overall security environment and risk management strategies.

